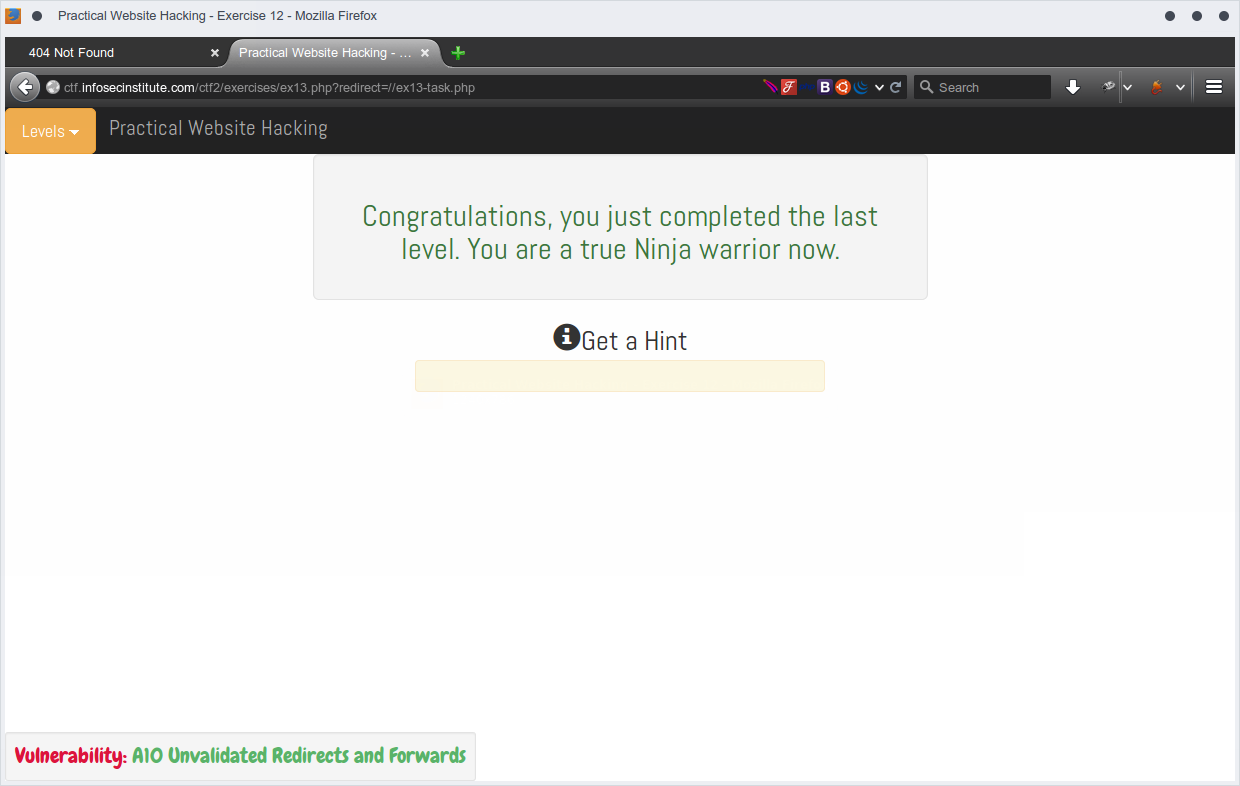
Level 13 | A10 Unvalidated Redirects and Forwards
Hmm, it seems that level thirteen is redirecting to this page. Why do not you analyze the redirect and search if the redirect is validated thoroughly. If not, you want to redirect to a page on a remote server and send links to people fooling them to think they are accessing a different domain.
Target:
Tools:
- Firefox
- BurpSuite
click on Level 13 and Intercepting the request, it was like redirect to (http://ctf.infosecinstitute.com/ctf2/exercises/ex13.php?redirect=ex13-task.php)
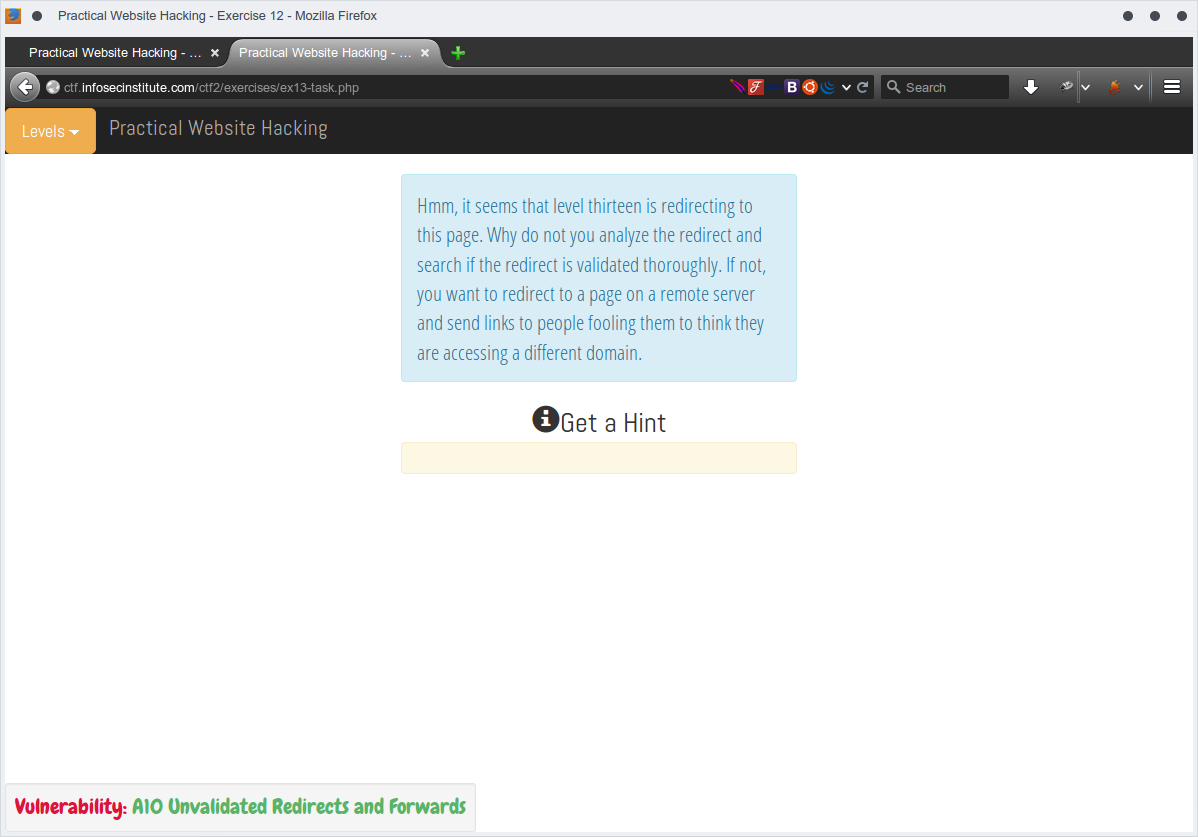
There is an interesting redirect up there,, let's to try manipulate it to be
GET /ctf2/exercises/ex13.php?redirect=attacker.zone HTTP/1.1 Host: ctf.infosecinstitute.com User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:38.0) Gecko/20100101 Firefox/38.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate Referer: http://ctf.infosecinstitute.com/ctf2/exercises/ex12.php Cookie: PHPSESSID=7v78334lr06v6j051f4epsj3e6; welcome=yes Connection: keep-alive
Tried to add arbitary url like http://attacker.zone but It gives me error Bad Redirect Parameter
aslo tried to use see if the condition is it to match a .php at the end of the file name like
http://ctf.infosecinstitute.com/ctf2/exercises/ex13.php?redirect=http://attacker.zone/hi.php
But it gives me Not found error.
finally I tried to add // before the script name ex13-task.php and it works
http://ctf.infosecinstitute.com/ctf2/exercises/ex13.php?redirect=//ex13-task.php